There is something in the news every day about a new phishing attack. Some of the most recent attacks have occurred because of simple oversight – a username and password that wasn’t purged from the system after an employee left, or a password that wasn’t changed after it was found on the dark web.
Security breaches are a daily occurrence, making headlines on a regular basis.
Costly incidents are happening more and more frequently across all industries and businesses.
Every business leader is charged with beefing up IT security and protecting both proprietary data and customer information, but network security alone is no longer enough.
Passwords Are Not Enough
Passwords are not sufficient for securing accounts or network access. Not only do we all reuse passwords regularly, but it’s the easiest security to steal, either through brute force attacks or through phishing attacks. It’s almost a guarantee that at least one of your employees is using the same password for their Uber account or pizza app as they are to access your network. Your data is not safe without taking more extreme measures to protect it.
In addition to developing a zero-trust culture and policies that provide essential guidance for resisting phishing attacks, organizations need to consider moving beyond simple password access to their networks.
Multifactor authentication (MFA) is one of many new layers of security that Calgary businesses must consider to thwart additional attacks.
What Is Multi-Factor Authentication?
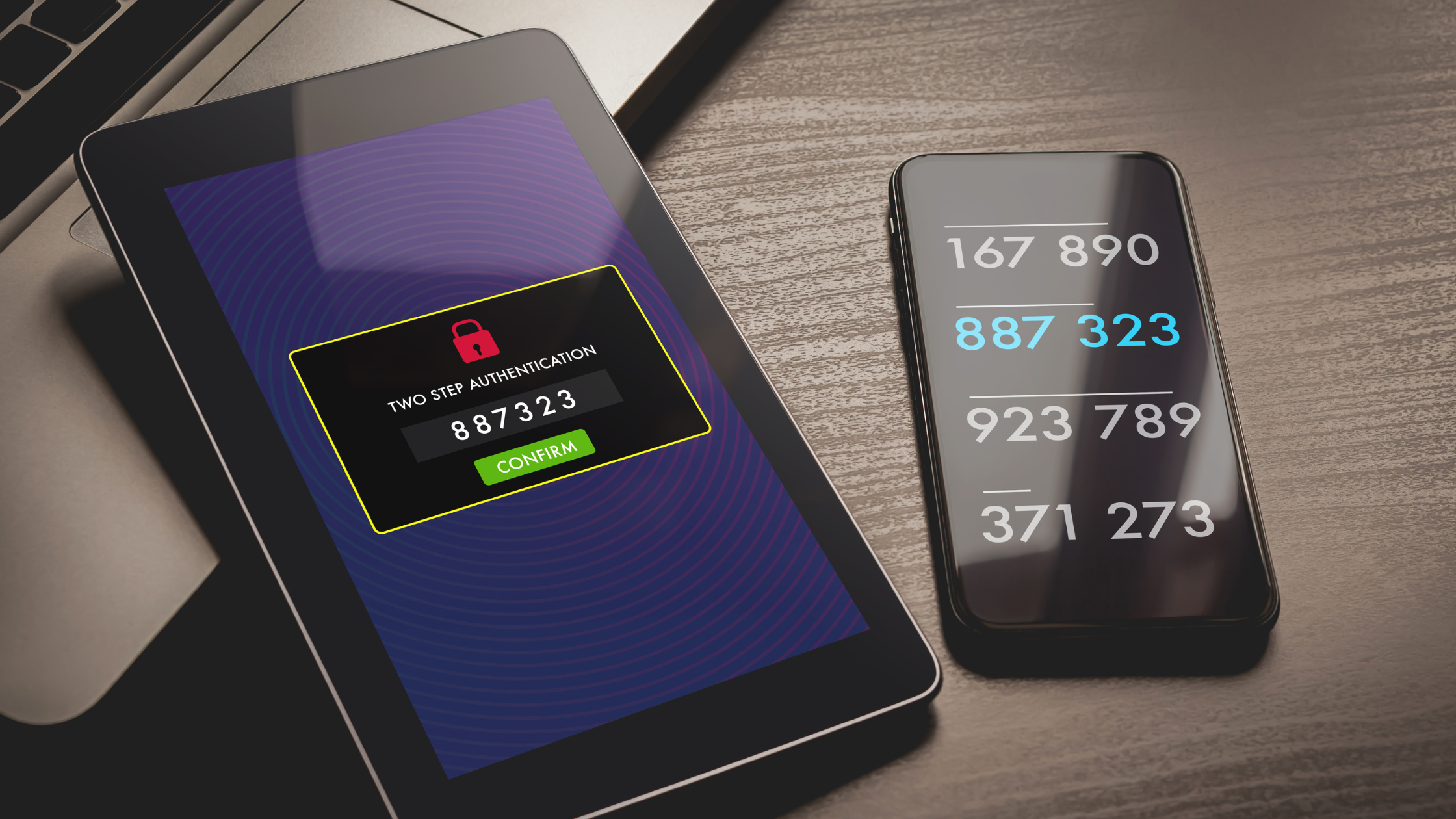
Multifactor authentication, sometimes called two-factor authentication, is a crucial security layer that requires more than one authentication method to verify a user’s identity and allow access.
It blocks all access to a device, network, or terminal unless two of three factors are provided: something you have, something you know, or something you are.
These independent identity authorizations include a password, a security token or code, and often, a biometric verification such as a fingerprint.
How Multifactor Authentication Works
MFA makes it virtually impossible for someone to hack into the protected account.
Most consumers use multifactor authorization all the time without realizing it. When you use a bank’s ATM machine, you swipe a card and enter a pin. That’s MFA at work. So is having to put in an Authy code once you’ve entered your username and password to log into your checking account.
Requiring MFA for access to your business network isn’t troublesome or time-consuming. It’s the smart way to add a layer of protection that prevents unauthorized access to your network.
Calgary businesses need to begin recognizing that employing MFA as part of their overall IT security strategy can literally prevent security breaches by implementing MFA as a part of their overall IT security strategy.
The combinations for multifactor authentication are limitless:
- Card swipe + pin
- Username + password + texted access code
- Card swipe + fingerprint + security question or password
A Brief History of Multi-Factor Authentication
Authentication is not a new idea when it comes to security. Unlocking a door, providing your identification to make a purchase, and even showing your passport are all forms of authentication. But since the advent of the computer, authentication has become a significant and growing piece of the security puzzle – and multi-factor authentication is simply a more complex way to gain access to something that single-factor authentication or two-factor authentication.
Two-factor authentication became commonplace in the 90s, but as cyber criminals become more sophisticated in their efforts to break into networks, steal data, hold it hostage for ransom, and otherwise wreak havoc, MFA has become an essential layer of security.
Cyber Attacks Costs Everyone
The average cost of a data breach in Canada is $6.75 million, and half of all cyber-attacks on Canadian businesses are successful, with more than 51 percent of businesses reporting losses.
While multifactor authentication technology should not replace existing security (firewalls, malware detection, hosted email exchange, offsite backup and recovery), it should be used to augment security, making it far more difficult for anyone other than the intended party to access sensitive information.
Combined with other security measures, such as stronger employee passphrases, robust email security, and secure, locally hosted services, multifactor authentication is an essential element of your organization’s overall security efforts.
MFA can prevent hackers from achieving a brute force entry into your network. According to Microsoft, MFA can stop up to 99.9% of the attacks on your network.
It’s much harder to breach a network using a fingerprint or a one-time-use access code texted to a single mobile device than it is to guess an employee’s password that is likely written on a sticky note under their keyboard.
Why MFA Is Essential for Your IT Security
As technology fundamentally changes how we do business, serve customers, and meet compliance standards, business leaders must re-evaluate whether their current IT strategies are meeting their needs.
The Future of Multi-Factor Authentication
Next-gen MFA will make it easier for end users and harder for hackers. Passwords will (hopefully) become a thing of the past, as we move toward forms of biometric authentication.
Where biometrics were once expensive and difficult to employ, the technology has not only become more accurate but also more affordable. MFA before the ubiquity of smartphones was more difficult, but according to Mercator, 66 per cent of all cell phone users will use biometrics on their smartphones by 2024. This makes MFA far more convenient, since no special equipment must be installed. In addition to fingerprint readers, many smart devices now have voice and facial recognition security installed, providing a number of additional options.
Cyber criminals continue to get more sophisticated in their efforts to steal critical data – and it’s profitable enough to do so that they are not going to stop. The argument for employing multi-factor authentication as a condition of accessing your network and data – for employees, vendors, and clients or patients – is strong, regardless of your industry. From dentists and health providers who have compliance guidelines they must meet to oil and gas industry organizations whose data, in the wrong hands, can devastate entire communities, MFA can provide a significant layer of protection.
The ITeam is committed to helping Calgary- and Alberta-based businesses develop proactive IT strategies that keep them competitive. Contact us to learn more.