IT Email Security
Many cyber threats target email because nearly everyone in developed countries uses email and every email account has extensive connections to other people. A successful breach of one email account can result in an eventual breach of thousands or even millions of other accounts. View our easy to use email security guide below; then discover how you can transform your employees from your weakest link to your first line of defense through security training.
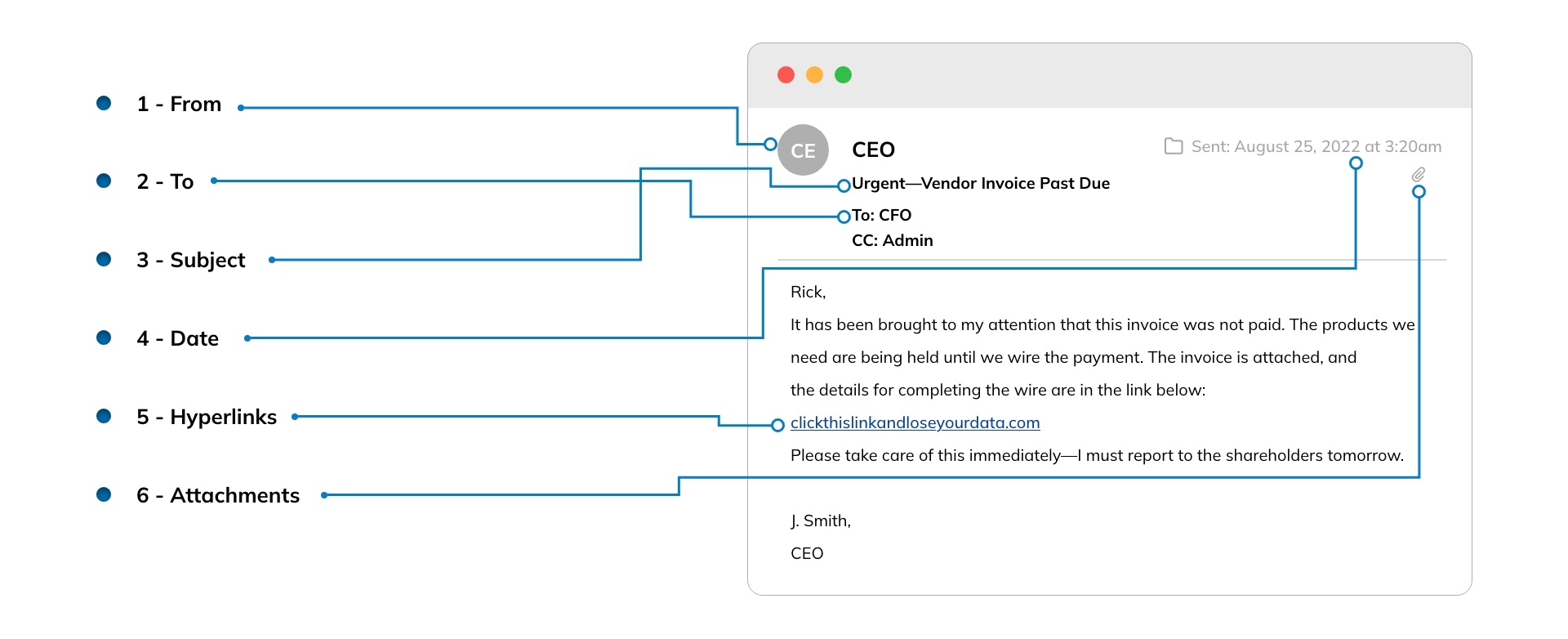
The ITeam Email Security Guide
Follow these steps before you click: