Looking for a Managed IT Service Provider in Calgary?
The ITeam is an award-winning managed services provider. Our expert managed IT support is designed to meet the needs of businesses in a variety of industries in Calgary. Managed IT makes IT support costs more predictable and manageable. Our service combines fixed-rate services with 24/7 support. As a result, you get a proactive IT solutions and experts you can count on.
What is managed IT service?
Managed IT brings the expertise you need to help your organization remain operational and competitive. As a top managed services provider in Canada, we do this in the most cost-effective manner.
What’s included in The ITeam’s managed IT support?
Benefits of IT Managed Services
Going to the dentist for regular cleanings can help prevent cavities. Similarly, managed IT services can help prevent pain for your organization. To remain competitive, compliant, and secure, organizations must be proactive. To do this, they must take preventative measures against risks. Therefore, we don’t wait until you have a toothache to worry about. Service companies like The ITeam do everything we can to keep you from having one at all.
- Cost Predictability
Turn IT costs into a fixed monthly cost. Managed IT can help you avoid unexpected capital expenditures. Then you can invest in other business needs. - Stability
Without a doubt, business continuity is crucial for continued growth. Service companies like The ITeam monitor and support around the clock to ensure uptime in case of unexpected IT network failures. - Proactive IT
Proactive IT management leads to more reliability. A managed service provider can detect issues in your business before they are problems and prevent them from becoming worse.
Outsourced IT Services
Outsourcing IT services to a managed services provider helps Calgary organizations extend their internal IT teams. Organizations gain the benefits of an experienced and established team of a managed services provider without incurring the sometimes-exorbitant cost of hiring additional internal IT staff or maintaining an entire IT support department. Outsourcing IT services to a Calgary managed services provider can give your business the opportunity to focus on business operations, strategy, relationship building, and growth – all while having the peace of mind to know that you have an expert team monitoring your network, installing patches to software, and making sure servers are up and running. Outsourcing IT support by choosing a managed services provider is a proactive method of protecting your business, your network, and your data.
- Reduce Costs
Outsourcing IT services to a managed IT service provider allows companies to access a pool of skilled professionals without the overhead costs of hiring and maintaining an in-house team. This MSP partnership can lead to significant cost savings in terms of salaries, benefits, and infrastructure. - Scalability and Flexibility
Outsourcing to an MSP is a a strategic solution that allows a business to scale their IT resources up or down based on demand and business productivity. This flexibility is particularly beneficial for seasonal or project-based work, ensuring that companies have the right level of support from service companies without the long-term commitments. - Continuous Operations
By outsourced managed IT support to an MSP partner, a business owner gets 24/7 support – option for business leaders that helps ensure critical IT functions are monitored and addressed at all times, reducing downtime and enhancing the overall reliability of IT systems.
Managed IT Support
Managed IT support is a strategic solution for most Calgary organizations, but if you are a small- and medium-sized enterprise (SME) without the extensive budget required to maintain your own internal managed IT solutions team, partnering with an MSP for managed IT solutions can be a cost-effective solution. The cost and complexity involved in recruiting and assembling your own in-house managed IT support team can take you away from focusing on your core business and strategic goals. Managed IT companies can help you achieve your business goals, remain cybersecure, and achieve compliance.
- Increase Efficiency
Your Calgary managed service provider takes over some of the heavy lifting – taking a proactive approach to managed IT solutions for everything from managing software licenses and patching to 24/7 monitoring – giving you a competitive edge to focus on your core competencies and goals more efficiently. - Stronger Cybersecurity
Managed IT companies provide you with access to robust security measures to protect your data and systems from cyber threats. With regular security audits and updates, you can ensure that your business plan is up to date with the latest security technologies – all while realizing a reduction of costs. - Improved Customer Experience
Managed IT companies work behind the scenes ensuring the security, reliability, and uptime of your network, you can deliver a better customer experience to your customers, no matter what industry you’re in.
Who Needs Managed IT Services?
A managed service approach gives businesses comprehensive security. This includes customized backup and recovery solutions as well as secure cloud storage and hosting. Our team will work with you to create a customized plan that meets your needs and requirements.
During your initial business assessment, we will:
- Identify weak areas and security risks
- Review everything such as network security, systems, application patching, backup and recovery services
The list of reasons why people choose a managed service provider includes:
- Stable cost structure – Improved budgeting and predictable annual operating expenses
- Reduced downtime – To remain competitive, agile, and capable of continued growth
- Compliance – We help you meet requirements for regulatory purposes
- Prevent data breach – Prevent unlicensed software, poor infrastructure, or inefficient resources (human and machine) from putting you at risk
- Peace of mind – We are on the job with 24 hours a day, 7 days a week monitoring
Managed IT Service for Every Market
Our team has extensive knowledge and experience in various industries in Alberta. As a result, when you partner with us for your IT management solutions, you get a support system that truly understands your needs and improves the likelihood of business success. We provide managed IT solutions to organizations in every industry, including both oil & gas and healthcare. In addition, we work with legal, financial & accounting services, construction, small businesses, and more.
Our Process
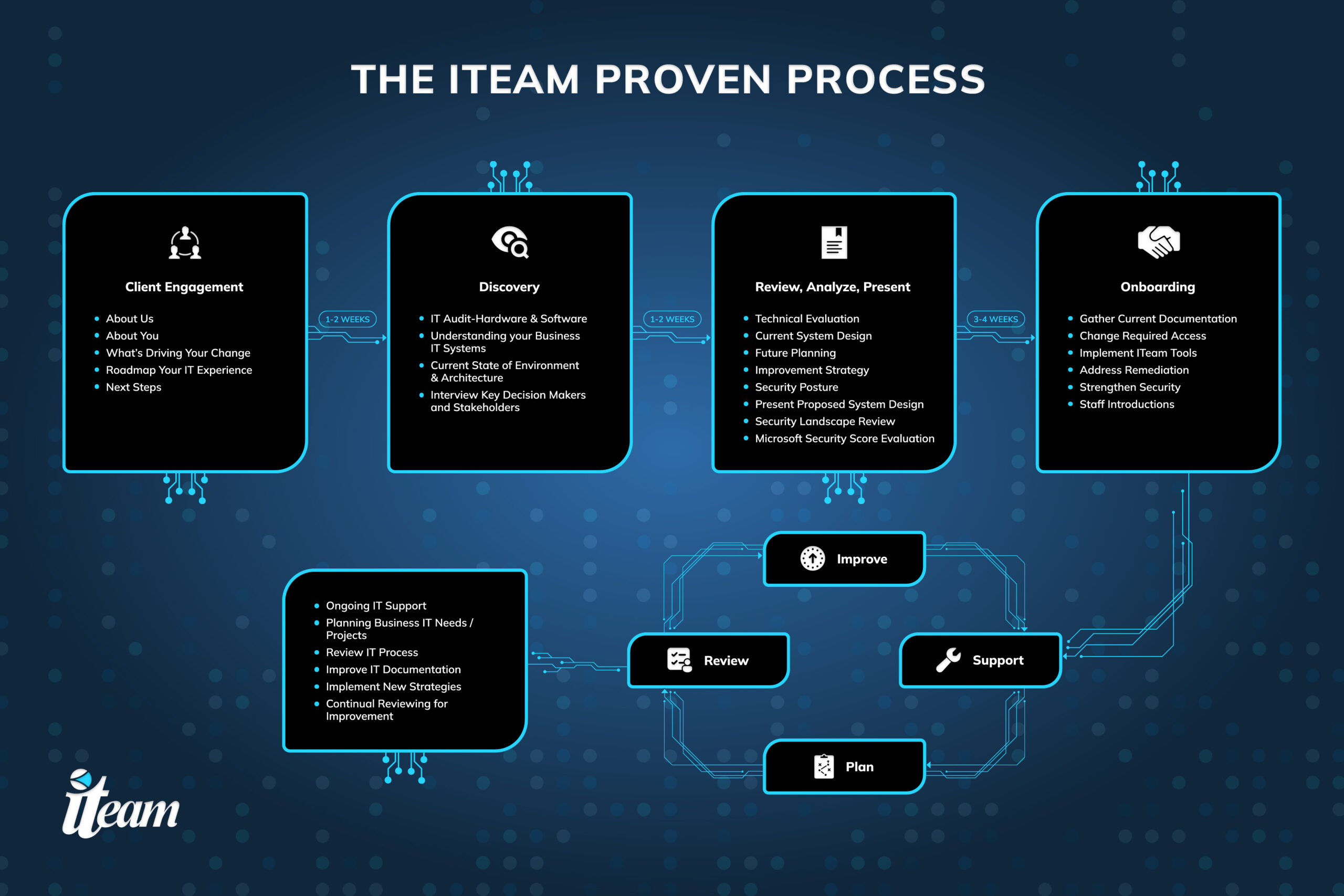
Why Choose The ITeam?
With our managed IT solutions, we make sure your needs are met. We develop a customized plan that is right for you, so we work closely with you and your team.
- Server Hosting & Co-Location – Our server is hosted, managed, and supported locally in Calgary. This ensures the protection of your data and the continuity of your business.
- Offsite Backup – We will ensure that your data is always secure and protected from theft, fire, and flood.
- Email Security & Employee Training – A successful breach of one email account can result in a breach of thousands or even millions of other accounts. The ITeam offers security training to keep your employees vigilant and aware of the risk.
