Every business faces the risk of a ransomware attack.
Unfortunately, those attacks continue to be more sophisticated as technology advances.
It is much more cost-effective and efficient to have replication and cloud backup services than paying a ransom and working to decrypt attacked files.
In the event of a data breach, ransomware attack, or natural disaster that damages your network, a disaster recovery plan will help your business quickly and easily recover from the loss.
A backup and data recovery plan is an essential risk mitigation strategy for business continuity – one that can be very costly if ignored.
Our professionals at The ITeam have created an extensive article on how to create an effective disaster recovery plan.
What is an IT Disaster Recovery Plan
For businesses, an IT disaster recovery (DR) plan is an action plan that can be implemented in a worst-case scenario catastrophe.
If the worst happens and you’re not able to operate your business from its normal location or use your network, an effective disaster recovery plan will let you continue to meet your customers’ needs.
Why Should My Business Have a Disaster Recovery Plan
It’s a matter of when, not if your business will experience some kind of natural catastrophe or cybersecurity breach.
Your business continuity depends on having a disaster recovery plan.
Offsite backup and data recovery are critical to all businesses, no matter their size.
A plan should be created before any disaster occurs.
In any of the following scenarios, having an IT disaster recovery plan gives you the ability to continue operating.
- Your building suffers from a fire and is inaccessible for several days
- There is a natural disaster in your city that makes travelling to your business impossible
- You must operate from an alternate location due to an unanticipated emergency
- Your network is compromised by malware, ransomware, or direct attacks
A disaster recovery plan allows your business to:
- Continue operating even when your building is inaccessible
- Minimize downtime
- Protect your customers
- Continue communicating with customers, vendors, and employees
- Prevent the need for paying ransomware should you be a victim of a hacker
- Reduce costs
- Improve customer service
Backup and Replication
At The ITeam, we use Veeam to deliver advanced image-based replication and secure your data in any disaster.
Veeam is a cloud data management software that provides data backup and recovery, data protection, data security, and data management.
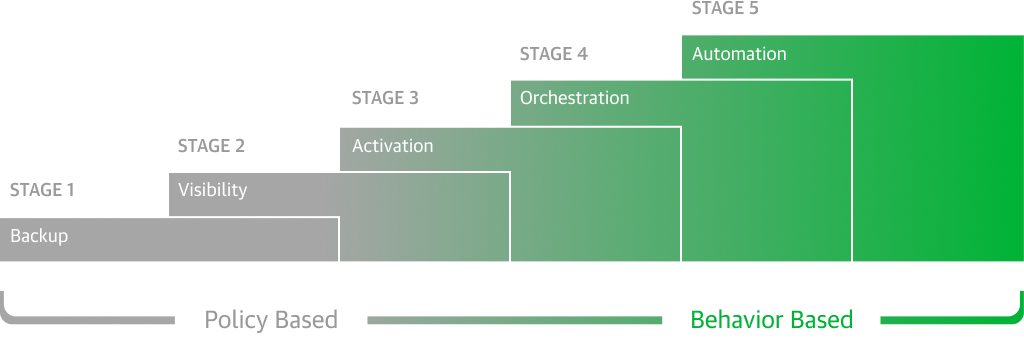 Including image-based VM replication in your disaster recovery plan can help avoid data loss and improve your recovery time for all applications and data, minimizing the impact on your infrastructure.
Including image-based VM replication in your disaster recovery plan can help avoid data loss and improve your recovery time for all applications and data, minimizing the impact on your infrastructure.
By employing a comprehensive disaster recovery plan, you will have access to the information your business needs to remain in operation, even if your facility is inaccessible or destroyed.
In case of disaster strikes, having cloud-based replication as part of your DR plan can be a great safety net.
It can provide:
- A copy of your virtual machine (VM) in a ready-to-start state, so if a VM goes down, you can immediately fail over to a standby VM
- Enhanced availability for any virtualized application
- Image-based replication on site for availability, or off-site for disaster recovery
- No impact on the production environment, performing replication from backup files
Create a Disaster Recovery in 5 Simple Steps
Your disaster recovery plan should integrate with your business in a way that prevents downtime from disrupting your business continuity, identifying:
What data you need to remain operational – The locations from which you would operate if your location is compromised
Communication Plan – Information on how you would communicate with your team during an emergency
Response Steps – Specific response steps in case of a data breach or ransomware attack
What Should Be Included in a Disaster Recovery Plan
Your plan should include secure, cloud-based disaster recovery as well as offsite data backups.
It should also include a plan for where employees will meet, how you will communicate with customers and steps you can take to minimize risk and maximize security:
1. Identify Critical Operations
In this step, identify what operations are critical to the function of your business that their interruption would impact your ability to operate.
This can be identified based on:
- The type of services and products you provide to customers
- The extent to which your business must operate from its specified location,
By better understanding the vulnerabilities that exist, whether they are specific to your industry or unique to your business, you can address the changes that need to be implemented to ramp up your cybersecurity strategy.
This effort may entail holding meetings with leaders in your organization who can help identify what risks would impede the operations in their department.
To ensure accountability, you should establish someone on your team to be responsible for the planning process.
Consider these questions:
- What elements of your business are so essential that you cannot survive without instant access to them?
- What information or data do you store that, if lost, would put your customers at risk?
- What proprietary business data do you need to protect in order to maintain your position in the industry?
2. Evaluate Disaster Scenarios
Evaluate different disaster scenarios and how they would impact your business.
What would you do if a natural disaster required your business to relocate?
What would happen if a hacker encrypted your files and demanded a ransom?
A one-size-fits-all disaster recovery plan does not always work for all scenarios.
Having your location damaged as a result of fire or a natural disaster necessitates different protocols than discovering a disgruntled employee who has compromised the company’s security.
Work with all the department leaders within your company to identify all disaster scenarios and appropriate procedures for each scenario.
By doing this, you will be able to determine your recovery objectives and timeline once disaster strikes.
3. Create a Communication Plan
No matter what kind of disaster happens, a communication plan is essential to ensuring your business continuity.
Assign specific people to clearly articulated roles.
For example, if there was a fire that damaged the building, it might be the maintenance supervisor’s responsibility to notify the CEO, who would then trigger a cascade of communications to be disseminated to staff.
If the business must be closed or moved, develop a plan of action for making sure the customers understand what has happened and how to get in touch with you.
If phone systems are compromised, be sure someone is appointed to take responsibility for communicating via social media and monitoring social media for customer inquiries.
If there is a data breach, your communication plan should also include both the required regulatory communications and the public relations communications to assure stockholders and customers of the actions you are taking to protect them.
It should also include emergency contact information for your managed services team who will help you through the recovery process.
4. Develop a Data Backup and Recovery Plan
Planning for a disaster of any kind is essential for every business that wants to remain functional, whether a minor malfunction occurs (a server fails, an employee deletes essential information) or a dire situation threatens to disrupt your business continuity altogether.
Although the goal is to avoid a breach altogether, cyberattacks are inevitable.
It is critical that you have a plan in place to rectify and minimize ensuing damages.
A strong response plan involves a team of IT personnel dedicated to fixing the problem, monitoring for further intrusion, and containing the existing data breach.
Define Employee Roles
Just as every employee has a role in maintaining the security of your organization, every employee can have a role in the recovery.
You can delegate roles by department or by seniority level, but every person should play a part in helping the company recover.
Identify Mission-Critical Data
One of the most important considerations in creating an organization’s disaster recovery plan is determining what information is crucial to keep the business operational.
Ideally, you will be able to create a disaster recovery plan that is comprehensive enough to keep you operational in any situation and flexible enough to meet your specific needs.
From client data to secure processes, from account detail to current project notes, your offsite backup should include the information needed to continue operating if returning to your main business location is not an option.
Such information may include emails, documents, contracts, images, tax records, applications and other rudiments necessary to conduct the day-to-day operations of the business.
Establish your plan in writing, specifying not only what you need to recover but where you would be able to recover it if your own network is compromised.
Your plan should include:
- A checklist of all equipment and data required to operate
- Contact information for your 24-hour recovery team (both internal staff and your managed services team)
- Alternative meeting locations
- Communication assignments and action steps
- A checklist of all the steps that must be taken and what employee is assigned to ensure their completion
Establish a Post-Disaster Follow-up
The information gained from any disaster your business experiences can be used to create a better response to the next natural disaster or prevent future breaches.
Every breach offers both the organization experiencing the breach as well as everyone else a reminder of the importance of proactive security measures.
Any time a breach occurs, it reveals any weaknesses in security exploited by hackers.
Adjust your strategy to strengthen the weaknesses that were exposed.
5. Test Your Plan
Once you have developed a strong disaster recovery plan, test your plan.
Run a drill in which a natural disaster happens or simulate a breach.
Test your team to make sure there are no gaps in your plan.
If you identify gaps in the plan – communication gaps, security gaps, or other issues, strengthen your plan with additional steps.
It may not rain today or tomorrow, but when it does, you’ll be glad you have an umbrella
Traditional onsite physical backups simply do not provide adequate protection for your business.
Data backups stored at your physical location are subject to the same natural disasters that would compromise primary data systems.
If housed locally, they are vulnerable to the same potential cyberattack as the rest of your IT infrastructure, if administered internally.
Part of BCDR should include replicating applications and servers along with the data.
For those businesses who store data backups on site, recovery and restoration generally take much longer to complete.
Every hour, every day, and every week without data access is significant for most businesses.
Every business can do more to prepare for a natural disaster or cyber attack and increase their proactiveness, to ensure a rapid recovery.
These five steps will help you improve your disaster recovery preparedness.
In the past several years, there has been an explosion of large-scale, coordinated ransomware attacks striking multiple businesses.
- In 2017, WannaCry Ransomware impacted 190,000 organizations in more than 170 countries.
- In 2018, Meltdown and Spectre were revealed as “catastrophic” security vulnerabilities discovered in Intel and ARM microprocessors that left nearly every organization at risk.
- In 2019, there are more than 10 known ransomware threats and there have been successful attacks on hospitals, municipalities, and businesses around the world.
That doesn’t even begin to cover the number of data breaches that have occurred over the past several years that has resulted in personally identifying information (PIN) to be revealed about the users – from LinkedIn to Yahoo to Facebook.
Even if your company might not do business with one of these organizations, your employees do.
Employees are often the biggest risk to your organization because the password they use for their social networks or personal information found on there may also be the password they use to access your network.
These incidents highlight something we have said repeatedly:
Business continuity and disaster recovery planning is critical to all businesses, no matter their size.
Every organization faces the real possibility of a catastrophic event that could compromise its data integrity and threaten its very existence.
The ITeam Provides Essential IT Support to Businesses in Alberta.
We provide fully managed and personalized services designed to meet the needs of virtually any business.
Our team will work with you to customize a cost-effective solution and help you develop a comprehensive IT security strategy that will help you survive any threat, whether natural or human-caused.
Contact us to schedule a network assessment today.

